Tips
The native version of IntegrityChecker is officially deprecated. Please transition to IntegrityChecker java version (icj).
This pages offers some suggestions for using IntegrityChecker.
GUI tips
Selecting more than one folder to process
More than one folder can be selected at once:
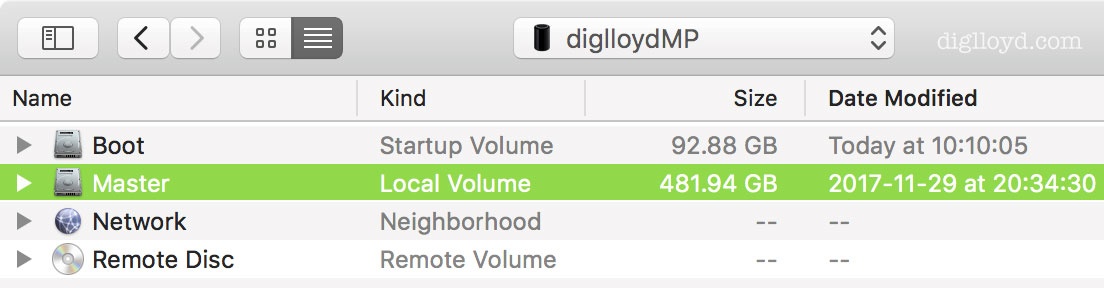
An entire volume can be selected, but be aware that macOS permissions may prevent IntegrityChecker from accessing off limits files and folders, such as those owned by other login account, the system, etc.
Command line tips
Volume name
You do not need to use /Volumes/Name for a volume eg the following are equivalent:
ic verify /Volumes/Master
ic verify Master
Multi-path
You can specify any number of paths for verify/update-*/status/clean.
or example, three volumes and ~/Library are specified here:
ic verify Master Backup1 Backup2 /Users/lloyd/Library
Performance
If you want to process more than one volume at a time (which are on distinct physical drives), running them in parallel is much faster than in one pass, because processing speed is almost always limited by disk speed. Therefore, more than one 'ic' can run in parallel with plenty of CPU power available.
This approach is the slowest, because the files are dealt with in order:
ic verify Master Backup1 Backup2 MyDVD
Instead, invoke a separate ic for each volume, each in a separate Terminal window. Each ic can then run on its own in parallel with the others:
ic verify Master
ic verify Backup1
ic verify Backup2
ic verify MyDVD
The .ic file and web servers
This tip applies to hardly anyone, but is worth mentioning.
IntegrityChecker creates its “.ic” file in every folder that you update. This file contains file names, dates and sizes.
To be clear, “security by obscurity” (not having the ".ic" file) is not security. Anything sensitive on your server should be properly protected with access controls.
Copyright © 2008-2010 diglloyd Inc, all rights reserved