Integrity Checker manual
The native version of IntegrityChecker is officially deprecated. Please transition to IntegrityChecker java version (icj).
NEW! Now includes a cross-platform JAVA version for macOS, Windows, Linux. More info...
IntegrityChecker™ provides ultra-efficient validation of your data, including your originals and backups. Even single-bit errors are detected, anywhere in a file.
The integrity of files can be validated at any time. The process is simple:
- Update the volume(s) or folder(s) (this compute the hashes and stores them in the “.ic” file in each folder).
- Verify the volume(s) or folder(s) from step 1.
It’s the perfect tool when moving data (backing up, switching systems, etc), because you can verify that all data has 100% fidelity to the original copy. And you can do so a day, a week or a month later, an important consideration if a system meltdown requires restoring all your data.
It doesn’t matter if the data is on a hard drive, SSD, BluRay or network. The only requirement to 'verify' is that 'update' has been done before— in other words that the file hashes have been computed and stored in the hidden “.ic” file in each folder. Of course, addition of new files does require that 'update' be run to “incorporate” hashes for the new files.
Example scenario
Problem to solve: you want to upgrade a hard drive to a larger one. Follow this process:
- Update the volume / drive.
- Make the backups of the volume; verify the backups (to be certain they are perfect copies).
- Remove the old drive (set it aside for safekeeping), install the new drive, transfer the backup to the new drive.
- Verify the new volume / drive.
Any similar scenario works the same way, and is in fact even more flexible: partial copies are fine; all that matter is that any folder to be verified has its hidden “.ic” file in place from a previous update. So it doesn’t matter if that folder is a 2nd or 3rd or 10th generation copy of the original.
Commands
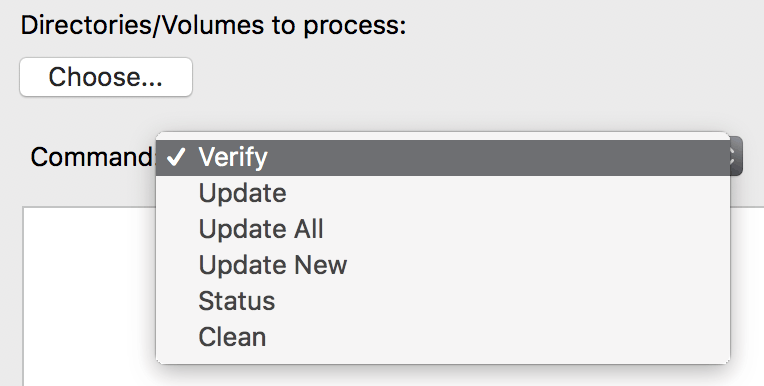
IntegrityChecker™ offers the following commands:
- verify — verify files for integrity, flagging those changes by date or size, and especially those that have changed content;
- status — quickly show status eg new files and/or size/date change (does not validate contents);
- update — update files that are new or have changed date or size;
- update-all — update all files, whether or not they already have validation info;
- update-new — update new files (only);
- clean — remove “.ic” validation files;
GUI vs command line
These are “one click” operations designed to provide useful results with no fuss.
While the GUI is convenient, the command line offers the most flexibility for users with more demanding needs.
Why use it? PERMALINK
IntegrityChecker validates only those files that were previously hashed; it cannot validate new files that were never before processed (no validation info).
Why is it better than a backup program that checks files?
Check anytime — IntegrityChecker can check any backup containing the validation info (“.ic” file) at any time.
Any media — works on any media, including hard drives, SSDs, CD or DVD or flash drive. Since the validation information is carried in the same folder as the files themselves, it “goes along for the ride”, to check today, or a year from today.
Ultra-efficient — IntegrityChecker also runs as fast as your drives can go, so validating your files is not a tedious experience.
Backup validation
Before making a backup, run IntegrityChecker on all the folders to be backed-up. Later, when the backup is complete, run IntegrityChecker on the backup to verify that all files are 100% accurate. You can repeat this process a day or a month or a year later to validate older backups, including those on CD or DVD. Since validation reads all the files, it is also a good “sanity check” on the health of the drive or CD or DVD itself.
When restoring from a backup, you can verify the backup first, or simply restore your files and then verify the restored files. In this manner, you can know for certain that the files you’ve restored are perfect.
Data transfer
Data transfer is essentially the same as backup, but it’s more about moving files to another computer, to another drive, etc. Follow the same process as for backup, and be assured that your files are perfect after the transfer.
Malware heads-up
Malware and ransomware can damage or encrypt your files. IntegrityChecker will flag all files that are different and will barf if its own files are damaged.
What’s changed on the system
Especially with multiple users and/or large data sets, you might want to see which files have changed. Changes include not just legitimately-changed files, but insidious corruption by software or flaky hardware, or a CD or DVD that is damaged.
IntegrityChecker can also be used on system software, but you’ll have to run with privileges using the 'sudo' command, to allow IntegrityChecker access to protected folders (it’s as easy as typing sudo in front of the command).
Copyright © 2008-2010 diglloyd Inc, all rights reserved